15 min reading Sat Apr 23 2022
How to manage unresponsive vendors in your third party risk management program?

When it comes to third-party risk management, one of the biggest challenges you can face is dealing with unresponsive vendors. This can be a frustrating experience, especially if you are looking for answers about potential cyber risks. In this blog post, we will offer some tips on how to deal with this situation. By following these steps, you can quickly identify and mitigate any potential cyber risks associated with that vendor.
But first, let's dive back into the concepts of a third-party risk management program (TPRM) and why you should set one up.
What is a third-party risk management program?
A third-party risk management program is a process that organizations put in place to assess the risks associated with third-party relationships. These relationships can include business partners, suppliers, vendors, and sometimes even customers. Within this blog post we'll limit to third parties being suppliers and/or vendors.
The goal of a TPRM is to ensure that the organization can identify, assess, and respond to any potential risks, such as cyber threats, vulnerabilities, or any business operation risks, posed by these third parties. This helps protect the organization from potential data breaches, financial losses, and other damages.
A well-thought third-party risk management program (or sometimes also called a vendor due diligence or vendor risk management program) will not only help you to effectively surface potential risks but will also help you to do it efficiently and thus limit the overhead in executing such a process.
What is the difference between third-party risk management and supply chain risk management?
The main difference between third-party risk management and supply chain risk management is that third-party risk management focuses specifically on the risks associated with third-party relationships, whereas supply chain risk management includes risks from third parties as well as those from within the organization's own operations. Think about the flow of goods and services, but also about the flow of information, money, and people. Specifically for cyber security; we're looking at all non-company owned assets that might pose a cyber security risk to the organization.
When it comes to third-party risk management specifically, the goal is to identify any risks that could arise from these relationships and put processes in place to mitigate them. This might include things like conducting background checks on third-party suppliers or auditing their security practices.
Supply chain risk management, on the other hand, takes a more holistic view of risks across the entire supply chain. This includes both external (as in we're working with an external provider) and internal risks (we're using a certain type of software library we have no control over). Log4J might be the best possible example here; lots of organizations are using different versions of log4J embedded in either self-developed software or off-the-shelf software. Either way, it's an asset, or part of an asset, on which we have little or no control and hence need to be scrutinized security-wise.
Why should you set up a third-party risk management program?
There are several reasons why you should set up a third-party risk management program. Here are some of the most important ones:
- To protect your organization from potential cyber threats and data breaches
- To comply with industry regulations (compliance and regulatory requirements such as GDPR, HIPAA, PCI DSS,...)
- To limit the impact on critical business operations in case a vendor gets compromised
- To reduce financial losses and limit or prevent data breaches
- To improve your organization's reputation
- ...
There are a lot of different reasons organizations choose to implement a vendor risk assessment program but it boils down to; when I have a high-risk supplier or vendor, how can I make sure we're aware of all the potential risks, can determine the risk level, and put controls in place to limit those risks?
5 Steps that define a good TPRM program
Now that we know why you should have a third-party risk management program, let's take a look at the steps that define a good TPRM program. These steps will help you to effectively manage the risks associated with your third-party relationships:
Develop and implement a TPRM policy
The first step in setting up a third-party risk management program is to develop and implement a TPRM policy. This policy will provide the framework for how the organization will assess third-party risks. The policy should include details on how the organization will identify, assess, and respond to any potential risks posed by third parties, and which type of risk will require which type of response. I.e. an operational risk will require a different approach than a reputation risk (think about business continuity versus brand protection). It should also outline which areas of the business are most critical and need to be protected.
Create an inventory of your vendors and suppliers
The next step is to create an inventory of all your vendors and suppliers. This will help you to quickly identify and assess any third-party relationships that pose a risk to your organization. The inventory should include the name of the vendor, contact information, what type of services or products they provide, and how long you have been working with them.
Determine how you will assess the risk level for each vendor
Now that you have created an inventory of your third-party relationships and assessed the risk level for each one, it's time to start mitigating those risks. You can do this by implementing different controls depending on the risk level. For example, if a vendor is deemed high-risk, then you may want to require a security questionnaire to be completed or even an on-site audit. You could also opt for a combination of continuous monitoring through a security rating system combined with a bi-yearly ad hoc self-assessment security questionnaire.
Address the third party security risks
Once you have implemented the controls, it's important to address the third-party security risks in your risk management plan. This will ensure that the critically important third-party risks are managed on an ongoing basis and that any new or updated risks are quickly identified and mitigated.
Define a vendor offboarding process
The final step in a third-party risk management program is to define a vendor offboarding process. This will ensure that when it is time to terminate a relationship with a third party, the process is smooth and doesn't have a negative impact on your business.
Managing third party vendors
Now that we have looked at the five steps that define a good TPRM program, let's take a look at how to manage your third parties.
Onboarding vendors in your third party risk management program
An important step in managing third-party vendors is to onboard them into your TPRM program. This can be done in a few different ways, but the most important part is to ensure that all third-party relationships are captured in your inventory. You can do this by requesting a list of all your vendors and suppliers from your finance or procurement department.
Another option is to use specific tooling that can generate a list of vendors based on the services implemented in your technology stack. For example, an external digital footprint scanner or attack surface management tool can provide you with an overview of all vendors used to provide specific services such as hosting, web application development, etc...
What is the difference between critical and non-critical vendors?
Now that we have looked at the five steps that define a good TPRM program, let's take a look at how to differentiate between critical and non-critical vendors. Critical vendors are those that pose a high risk to your organization if they were to be compromised. These are the vendors that you need to focus on most and put the most controls in place. Non-critical vendors are those that don't pose as much of a risk and may not require as many controls. However, it's important to remember that even non-critical vendors should be managed and monitored as they could still pose a risk to your organization.

Which vendor or supplier fits in which category is very dependent on your own organization, the business processes in which the vendor is implicated, whether or not they have access to any transactional and/or confidential data, whether they might impact business continuity should they get compromised, impact your organization's brand and reputation, different access policies handled by these companies, to which business department they report to, whether or not they handle confidential data such as PII data, source code, intellectual property, client data, whether their provided solution supports important business operations, etc ...
What about fourth and fifth party suppliers?
As you are probably aware, the third-party risk doesn't just stop at third parties. There is also the risk associated with fourth and fifth parties. Fourth-party risks are those that are posed by a third party's third-party relationships. For example, if Company A works with Vendor B, which in turn works with Vendor C, then Company A is exposed to the risk posed by Vendor C. This can be a very complex web of relationships to work with and can often be difficult to track. Fifth-party risks are those that are posed by a third party's fourth-party relationships. As you can see, it can quickly become complicated trying to track all of the different levels of risk.

The best way to mitigate fourth and fifth-party risks is by implementing a third-party risk management program that includes the five steps we have discussed. This will help you to quickly and easily identify and mitigate any risks posed by these third parties. You could then opt to include specific clauses on fourth and fifth-party risk in your third parties' contract and service level agreements.
Assessing the risk of working with a supplier
When you are assessing the risk of working with a supplier, there are a few different things you need to take into account.
The first is the impact that the supplier has on your organization. This includes both the direct and indirect impacts.
The second is the risk that the supplier poses to your organization. This can be assessed by looking at a number of factors such as how they store and protect their data, how secure their networks are, how they manage the (confidential) data you entrust them with, if they have had a data breach in the past and how they managed it, etc... This is where you determine if a supplier is critical or non-critical.
The third factor is how much effort it would take to replace the supplier if they were to stop working with you and look for an alternative supplier. This often depends on how integrated the supplier is into your business processes and what would be needed to replace them. REplacing a supplier often leads to interesting conversations with the organization's decision-makers and the different business units impacted by a vendor replacement. Onboarding new vendors can also be a very time-consuming task requiring interviewing multiple suppliers, renegotiating contracts, etc...
When assessing the risk of working with a supplier, it's important to consider all factors. This will help you to make an informed decision about whether or not to work with them.
We'll go through a few techniques for monitoring your third-party vendors in this section. Many organizations use a combination of one or more assessments methods. For example when onboarding a new company or supplier they specifically request a questionnaire to be filled out alongside a scan resulting in a security rating or posture analysis. Depending on the criticality of the supplier they then either go for continuous security rating monitoring only, combine it with bi-yearly or yearly questionnaires, and in certain events even request an on-site audit. Seeing the latter is rather expensive this is only performed in rare and critical cases.
Assessing the risk via security ratings
A means of assessing a supplier is via security ratings. External services can continuously monitor the attack surface or digital footprint of a vendor and gauge their security posture based on certain criteria. For example, have they correctly implemented their SSL certificates? Do they regularly patch their exposed systems? Is their DNS configuration secure? Etc ...
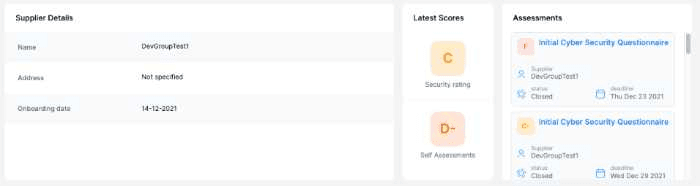
Security Rating follow up through the Ceeyu platform
By continuously performing these scans or assessments you can continuously monitor your vendor's security posture without requiring him to respond to complete a time-consuming questionnaire.
Assessing the risk via questionnaires
Another way of assessing the risk is by sending out questionnaires on a periodic basis, for example, every six or twelve months. This will give you an idea of how well the supplier is keeping up with their security obligations and if any changes have taken place that could pose a risk to your organization.
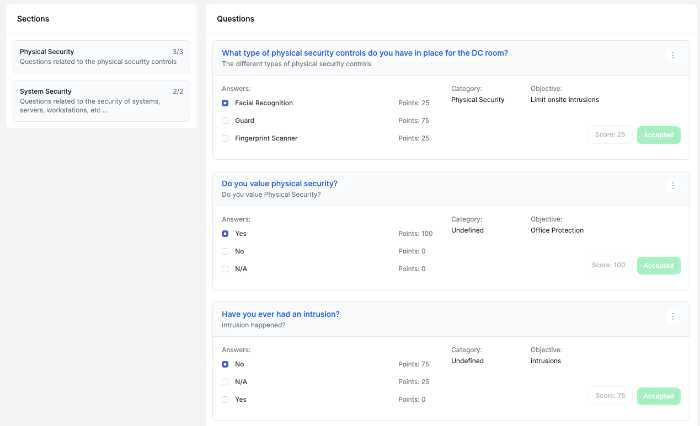
Questionnaire assessment through the Ceeyu platform
You can use this questionnaire as a way to gauge the severity of a data breach if one were to occur, and see what kind of notification and disclosure obligations would be triggered.
It's important to note that not all suppliers will fill out these questionnaires accurately or completely. In some cases, they may even try to hide certain aspects of their security posture in order to make themselves look more favorable. This is where you would need to use other assessment methods to get a more complete picture.
Assessing the risk via on-site audits
The third and most expensive way of assessing the risk is by performing on-site audits. This is often only done when there's a suspicion or doubt about the security posture of a supplier.
During an on-site audit, you'll have someone from your organization, or a contracted consultancy firm, visit the supplier's offices and take a look at their physical security, network security, data handling procedures, etc... Often times, you'll also be given access to their networks and systems so that you can perform your own independent assessment.
This type of assessment is time-consuming and expensive, but it can be one of the most effective ways of determining whether or not a supplier is a risk to your organization.
Continuously monitor vendor risk
No matter which assessment method(s) you choose to use, it's important to continuously monitor the risk posed by your third-party vendors. This will help you to quickly identify and mitigate any cyber risks associated with them.
You should trend the results over time so that you can see if any changes have occurred in their security posture that could pose a risk to your organization. And, if necessary, you can take appropriate action to mitigate those risks.
Communicating with your vendors
It's also important to communicate with your vendors about their security posture and any risks that you've identified. This will help them to understand the importance of security and how it impacts their business.
It's also a good way to build a relationship of trust with them so that they're more likely to cooperate when you need to perform assessments or audits.
Continuously monitoring your third-party vendors is an important part of any third-party risk management program. By using the methods described in this post, you can quickly assess and mitigate any cyber risks posed by them. And by communicating with your vendors, you can help them to understand the importance of security and how it impacts their business.
Communicating with your vendors starts early in the vendor management process, during onboarding and contract negotiation. This is where in fact you request them to participate in regular assessments via your third-party risk management process and stipulate the response times for questionnaires, communication channels, specific individuals involved in the process, and what will happen should they become unresponsive.
Managing unresponsive vendors or suppliers
Managing unresponsive vendors is one of the most difficult tasks in third-party risk management. By using one or more of these assessment methods, however, you can make an informed decision about whether or not to work with them. And by communicating with them early and often, you can help to build a relationship of trust that will make it easier to work with them in the future.
There can be multiple reasons for a supplier to become unresponsive.
Questionnaire fatigue
The most common reason is questionnaire fatigue. When you send out questionnaires on a regular basis - as you should - some suppliers will simply stop responding. They may get tired of answering the same questions over and over, or they may feel that they're not getting anything in return.
In some cases, the supplier may be unresponsive because they're having problems with their security posture and they don't want to report any negative news. This is where you would need to use other assessment methods to get a more complete picture.
Don't forget that you're not the only customer of that supplier and nowadays a lot of organizations enforce a form of vendor management in their vendor contracts.
My supplier never responded to start with, or, will I even get feedback on questionnaires from a big vendor like Microsoft or IBM?
You're not alone in this. Many organizations struggle with getting responses from their suppliers, especially large ones. And it can be difficult to know what to do when you don't get the answers you were hoping for.
There are a few things you can do to try and get the information you need:
- Follow up with them via email or phone call. Make sure to track who you spoke to and what they said so that you can follow up later if necessary.
- Use other assessment methods, such as on-site audits or third-party reports like security ratings. This will give you a more complete picture of their security posture.
- Contact your account representative at the supplier company. They may be able to help get the information you need.
- Talk to other organizations that are also doing business with the supplier. They may have had a better experience.
If all of these methods fail, and the supplier remains unresponsive, it may be necessary to terminate the relationship. This should always be your last resort, as it can be costly and time-consuming to find a new supplier.
That being said, you should ask yourself if you truly need a big vendor or supplier like Microsoft, IBM, Salesforce, etc... to answer your specific questionnaires. Seeing they cater to a lot of customers they likely won't have the time, nor are willing to perform the effort, to respond to every single questionnaire request.
As a countereffort, these enterprises often publicly release their GDPR, SOC2, PCI DSS, ISO 27001, CSA, and other certifications for everyone to look into. A simple search on their website can provide you with most of the guarantees you'll need.
Conclusion
No organization is immune to unresponsive suppliers. By using the methods described in this post, you can quickly assess and mitigate any cyber risks posed by them. And by communicating with your vendors, you can help them to understand the importance of security and how it impacts their business.
Remember that there not all vendors are equal. Depending on the criticality of your supplier you might want to assess them differently and communicate with them differently. But the goal should always be to maintain a relationship of trust and collaboration.
If you're struggling to manage unresponsive vendors, or if you have any questions about third-party risk management, please don't hesitate to contact us. We would be happy to help.
Jimmy is the founder, CEO and CTO of Ceeyu. Prior to founding Ceeyu, Jimmy was responsible for cybersecurity programs at large financial institutions and consulting company EY. Jimmy started his career as a security engineer. His duties included installing and managing firewalls, scanning infrastructure for vulnerabilities, and performing pen testing and ethical hacking.