8 min reading Sun Apr 03 2022
Why is Attack Surface Management important

The idea proposed in this blog post is to convince the reader that Attack Surface Management (ASM) is a journey of discovery.
ASM is where you approach the security of your digital footprint from the perspective of the threat actors. It is a process of continuous discovery, inventory, classification, and monitoring potential attack vectors of an organization's IT extended enterprise. The goal is to prioritize risks, stay ahead of threat actors and reduce data exposures to the entire internet.
What is an attack surface
The term “attack surface” is rather new. How we described it in a previous blog post is in the following way:
"Attack Surface Management is a cybersecurity exercise where software tools are used to continuously monitor the digital infrastructure of an organization. The goal is to have visibility on the exposure of known and unknown assets, in order to mitigate risk and reduce the attack surface. So the value added is having a big picture view of the vulnerabilities, hacker's attack vectors, and cyber security risks of exposed assets."
As a new term in the cybersecurity industry, attack surface management, is a mirror of its time. To be more precise, ASM reflects a change in managing security risk, introducing a new approach to cyber defense. It takes the attacker's viewpoint and maps the attack surface of an organization from the outside in aiming to have global visibility on the digital footprint.
What does an attack surface cover
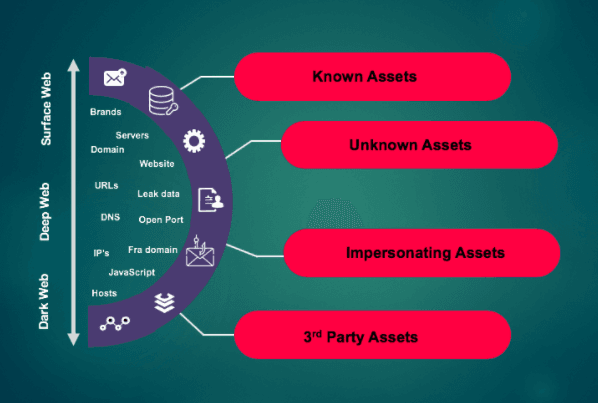
At a more granular level, an organization's attack surface is made up of exposed (known or unknown) assets such as:
- Digital assets such as exposed data, corporate website, third parties
- Infrastructure assets such as, DNS, email servers, IP addresses, IOT devices
- Increasing social media digital footprint due to digital transformation
- Forgotten assets or other related resources
The length and complexity of the list above goes hand in hand with business growth. At the same time, it is a result of the fact that digital transformation is encouraged, embraced, and rushed. All of these aspects combined, at the end of the day, presenting security teams and security managers with the ongoing challenge of mapping an organization's external attack surface and designing creative mitigation strategies.
At the moment, organizations that have a security program or a cyber risk management program have a head start. However, in order to improve their overall security posture, their entire environment should be considered.
What is the added value of attack surface management
On a high-level, attack surface management is important because it's about having eyes on the same things as the attackers. Thus, keeping up with the increasing sophistication of cyber attack techniques and preventing attackers to gain unauthorized access.
In terms of added value there are two aspects - one from a process perspective and one from a tooling perspective.
An effective attack surface management process is able to continuously discover any possible attack vector within the attack surface, as well as collect actionable threat intelligence.
From a tooling perspective, a successful attack surface management platform would enable security operations teams to reduce attack surfaces and automatically discover security issues before they become incidents.
How does attack surface management work
ASM can be integrated at a strategic level as well as at an implementation level, depending on the current security posture of an organization.
Strategy-wise, from an attackers viewpoint, there are a number of stages that lead up to gaining unauthorized privileged access. This is known as a cyber kill chain. This blog post considers the Cyber Kill Chain as the context in which ASM could fit into the offensive strategy of security teams.
MITRE ATT&CK uses adversary’s known Tactics, Techniques, and Procedures (TTPs) to describe the following stages of a kill chain model:
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Exfiltration
- Command and Control
In terms of high-level strategy, attack surface management could be linked with the reconnaissance stage of Discovery. This is due to the collection of network and end points information using automated tools, also known as footprinting.
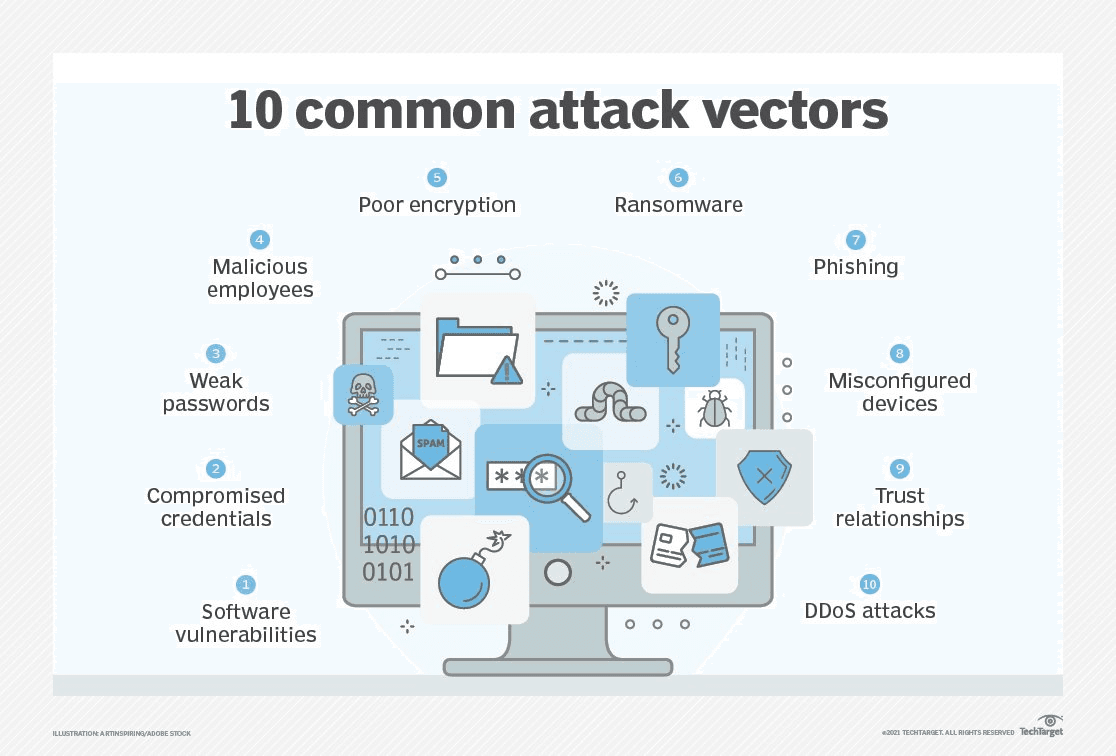
Implementation-wise, the way ASM works with regards to analysis and protection, could be seen as the equivalent of software vulnerability management with a focus on device settings and operating system exploits.
In more detail, on the one hand, vulnerability scanning identifies systems, devices, and applications that have known vulnerabilities. While this process might include some level of attack by exploiting some vulnerabilities, vulnerability scans can be complemented by penetration testing.
On the other hand, most full-scale penetration tests will include a vulnerability scan as part of a broader process. They can be very thorough in examining networks and application security. Starting with OSINT, the goal is to gain unauthorized access similar to an attacker, and find a possibility to compromise and exploit a system vulnerability.
What is the process of attack surface management
As we discussed above, attack surface management can become complex as it can include multiple processes. Keeping our eyes on the ball, the goal is improving the security posture and mitigating potential cyber attacks.
This blog puts forward what could be an ASM process from an IT Security viewpoint.
To start with, it is critical for ASM to maintain a continuously updated inventory of all known assets, unknown assets (i.e. shadow IT) , managed assets, as well as related resources.
A continuous discovery process is a key part of the attack surface management process, in order to have visibility on assets accessible from outside the organization. ASM-aside, such an asset inventory is an invaluable tool to understand your organization's attack surface and exposure to cyber threats and data breaches.
That being said, your average organization might already have one or multiple views on its third parties, all types of IT assets, or IOT devices. If we go one level deeper, at the data and software level, there are two key elements that need to be in place.
- On the one hand a complete data inventory, with a view on data classification/data sensitivity.
- On the other hand, an up to date and accurate software inventory. Easier said than done depending on the size of the organization. However, in a first step, having a solid system documentation is key in designing an attack surface management process.
Next, a proposed idea is to enable security teams to do their best work. Be it in security operations or in the IT department, it can be by adapting or expanding an existing IT security process to include attack surface management, or if an organization is mature enough, by using a dedicated attack surface management platform.
Another option here could be to piggybacking on an existing IT third party risk management process (TPRM). For an average organization this might be more difficult than for a large organization. Outsourced digital assets is where an organization has the least control and the most dependencies running, due to the diversity of cyber threats and the varying security posture of third parties.
In conclusion, an ASM process ideally follows the existing IT Security process. However, many organizations are at different levels of maturity in their IT Security processes. This is where ASM could also be seen as an accelerator as it can help complement the existing security strategy or build on existing results from other security exercises.
How attack surface management helps security teams
As we described above external attack surface management comes into play at a strategic level as well as at an implementation level. As such, an ASM strategy would consider a number of elements. Some of these elements are possible attack vectors mapped in a custom threat model, industry threat intelligence, key capabilities in IT and/or Security. All of these elements would further need to be linked to a security program in order to best mitigate risk of all internet exposed assets.
The value for security teams and security managers lies in improved risk management and the ability to stay ahead of the threat actors.
The need of an organization for IT risk mitigation has increased in parallel with the increase in shadow IT. In an ASM context this means unknown assets, rogue cloud-based applications, or simply forgotten IT asserts. This can lead to increasing attack surfaces, making it easier for attackers to find vulnerable IT assets and extract data. The risks that shadow IT presents are potential data breaches, data leakage, insider threat and the list goes on. Add to that TPRM and it becomes a hard to manage IT security challenge for any organization's security team.
This is where ASM can help the security team prioritize risks and focus on the high impact assets. By having an attackers view on the threats to your organization, you have a view on the potentially targeted critical assets. Considering this in your risk prioritization can help improve your organization's security ratings. Furthermore, if there's room for collaboration, you might help improve the security ratings of your third party vendors.
Real world examples of how your attack surface could impact your organization
Some real life scenarios where attack surface management could have helped prevent supply chain attacks, include SolarWinds and Log4J. In these cases, the assumption was that the third party vendors were secure, which turned out to be the opposite, and furthermore a way in for the attackers. Leading to third party data breaches rendering the life of security leaders and security teams a complete nightmare.
Another scenario is the Colonial Pipeline ransomware attack. As organizations are working with remote workforces due to the pandemic, the attack targeted remote services like Citrix, Remote Desktop Web(RDWeb), or remote desktop protocol(RDP).
In both scenarios attackers exploited a road inside the organization which was not mapped and monitored by security teams. As organizations grow their digital landscape it becomes increasingly difficult to have good visibility on all digital and IT assets. Reason why it is important to have complementary view on the attack surface that combines the inside-out view with the outside-in provided by ASM.
In conclusion
In the end, the hope is that this blog post convinced you that as the cliché goes ASM is a journey and not a destination. It is first of all a change in optics from the perspective of the threat actors instead of the usual organization-centric defensive view. The journey is a process of continuous discovery, inventory, classification, and monitoring of potential attack vectors of an organization's IT extended enterprise. Second of all, it can be a powerful catalyzer for the security posture of an organization. In the same journey, adapting or expanding an existing IT security process to ASM can add real cybersecurity value.
Get a view on your digital footprint and TPRM with Ceeyu. An all-in-one platform for cybersecurity ratings and third party risk management.
Get in touch at [email protected]



