
About 65% of vulnerabilities can be exploited remotely
The Stack
Penetration testing
Penetration tests (or "pen tests") have become the professional service of choice for many companies to bolster their cybersecurity defenses against external threats. Unfortunately, there is a lot of overhead involved in organizing a penetration test: you have to find the right provider, providing a good quality service at a reasonable price, identify the target applications or systems and define the scope, do the price negotiation and complete the paperwork. And a year later, this process starts all over again.
At Ceeyu, we offer hassle-free penetration testing. Because the penetration tests are part of your subscription with Ceeyu, we take the initiative to schedule them every year. Based on weaknesses we identify with our attack surface scans, we suggest targets for penetration testing. The results of the test are discussed with your IT team, and afterwards remain accessible via our web portal for follow up and mitigation.

The Stack
Automated scanning — including digital footprint mapping and attack surface monitoring — and penetration testing both have their pros and cons. Automated scans run continuously and can cover a wide range of IT and network assets but are more superficial, while penetration tests are more thorough but more limited in scope. When used together they are a match made in heaven. Using attack surface scans and monitoring, IT teams can inventory all externally visible assets and identify the majority of vulnerabilities. Pen tests can ascertain that no vulnerabilities have been overlooked and that vulnerabilities detected with attack surface scanning have been adequately addressed. For post-penetration test follow-up on mitigation actions, testing and monitoring, our attack surface analyses can be used.
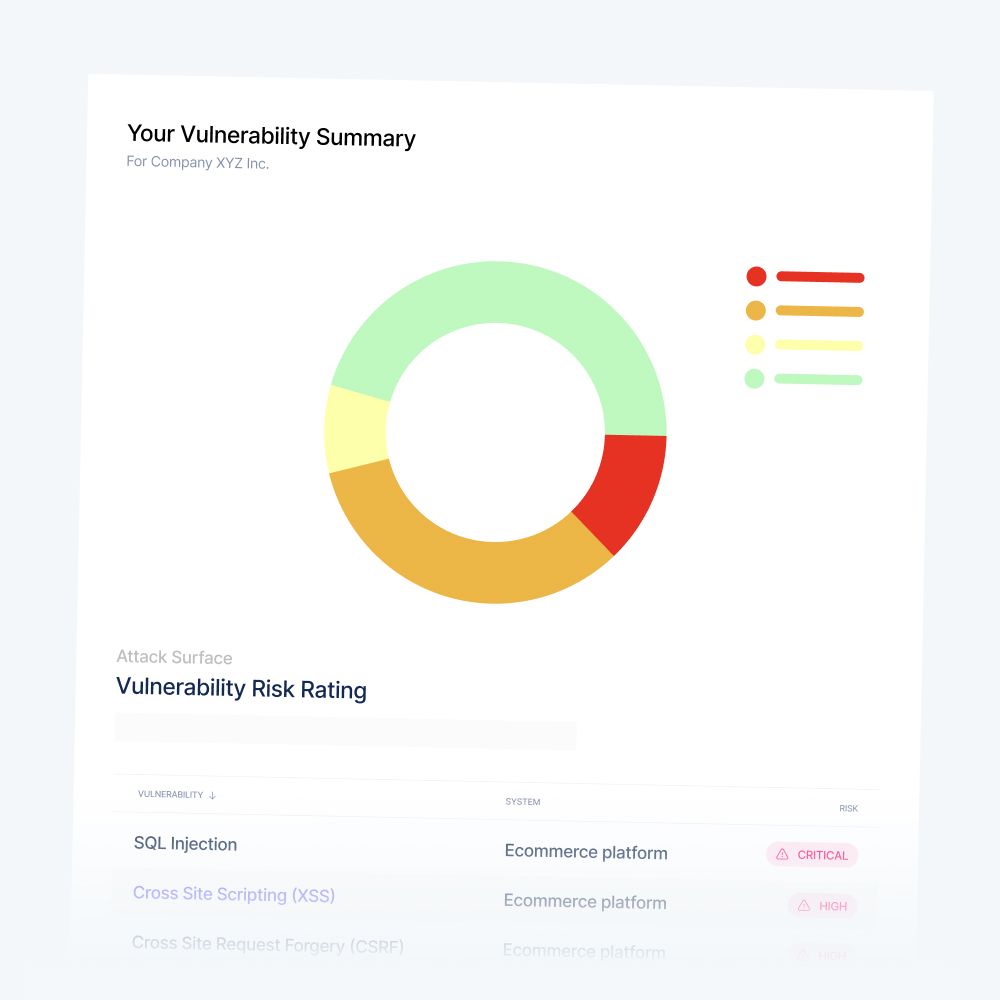
Based on our findings, we will propose one or more of the following services :
Do you have a penetration test in mind that does not fit into the above categories? No worries, we'll put together a custom pen test and find your gaps (if any).
Starting from the results of automated scans, Ceeyu saves valuable time compared to a "stand-alone" penetration test:
At the end of the penetration test, we save the report on our platform for future reference. Thus, risk identification and vulnerability management are centralized in one application.
Since you deal with only one party for all your external cybersecurity risk identification services, including digital footprint mapping, attack surface monitoring and penetration testing, you save valuable time and overhead!

With Ceeyu's penetration testing, you can zoom in on your critical applications to ensure they are free of remotely exploitable vulnerabilities.