5 min reading Sun Mar 19 2023
Active or passive vulnerability management – what’s the difference and which one is better?
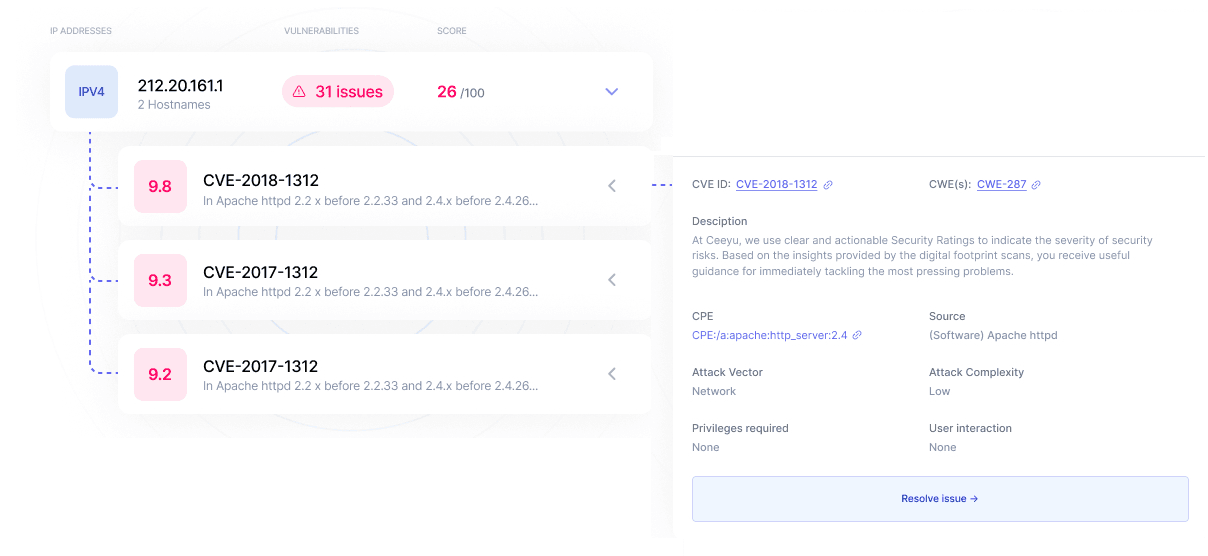
Vulnerability management is the iterative process of identifying and mitigating weaknesses in an IT or network system. It involves scanning for known vulnerabilities and patching or remediating detected flaws that pose a security risk. Vulnerability management is an essential part of cybersecurity. Before we get down to comparing active and passive vulnerability management, some definitions.
What are vulnerabilities?
The United States’ US National Institute of Standards and Technology (NIST) defines a software vulnerability as a security flaw, glitch, or weakness found in software code that could be exploited by an attacker (threat source). In 2022, a record 26.448 of vulnerabilities were reported, with 59% increase of the critical vulnerabilities. These are weaknesses that are easy to exploit and whose exploitation can have significant consequences, for example theft of confidential data (in reality, the criticality of a vulnerability is determined by a dozen of parameters, but it would take a full article to explain). Important to know is that around 65% of these vulnerabilities can be exploited remotely by a hacker.
There are four reference databases that collect reported and confirmed vulnerabilities:
- The NVD, or National Vulnerability Database, operated by NIST.
- The CVE, or the Common Vulnerabilities and Exposures database, managed by the MITRE Corporation, a US non-profit managing federally funded research and development centers in the United States.
- The CNNVD, the China National Vulnerability Database of Information Security, run by the Chinese national intelligence service, the China Information Technology Security Evaluation Centre (CNITSEC).
- The CNVD, confusingly named the China National Vulnerability Database, is nominally run by a Chinese non-profit, the National Computer Network Emergency Response Technical Team/Coordination Center of China (known as CNCERT/CC).
All these databases have around 200,000 vulnerabilities documented. The CNNVD has slightly more vulnerabilities listed than the NVD, with a 92% overlap between them.
In addition to the above public databases, there are several private providers that maintain databases with valuable information on vulnerabilities, including Qualys and Nessus.
What is passive vulnerability scanning?
A passive vulnerability scanner analyzes network traffic and documents to gather information about what types of systems and software versions are in use by a company. Based on the results, databases are searched for known vulnerabilities for those systems and software. This technique is referred to as passive, as there is no interaction between the scanner and the system. The scanner analyzes output of the systems, specifically, message fingerprints and file meta information.
Generally speaking, there are two main categories of passive vulnerability scanners; the internal vulnerability scanners, which are placed inside a corporation network corporation, and the external scanners, which scan for vulnerabilities from outside the network and provide more insight from the hacker’s perspective.
How does active vulnerability management work?
Active vulnerability involves actively scanning a network – interacting with the system - to detect and identify vulnerabilities by executing a series of tests in real time. Based on the analysis of the responses received (or the absence of responses) from systems connected to that network, the scanner assesses if there are weaknesses present. This can be done manually, as part of a penetration test, or through automated tools or services.
Active scanners send packets to endpoints and analyze the response to determine if there’s a vulnerability. However, they do not simulate an attack. These solutions are called cyber attack simulators.
Let’s have a look at the pros and cons of both approaches.
Pros and cons of passive scanning
The major advantages of passive scanning are:
- Passive scans are non-intrusive. They won’t trigger intrusion detection response systems. Also, they don’t interfere with the proper functioning of critical IT processes and systems.
- Because they are non-intrusive and harmless, passive scanners can work continuously, scanning the entire digital footprint of a company. They can be used to:
- Identify open ports that should be closed;
- View which services are available and running;
- Verify data in the IT Asset Management System or the Configuration Management Database, such as software and version (hereby also identifying potential shadow IT applications).
The disadvantages of passive scanning are:
- Scan results are often incomplete as not all systems disclose their software version. Often, this information is removed for security purposes.
- Because some software version information is omitted in network traffic, the search for a partial version number, or just the name of the software, results in a long list of vulnerabilities that do not apply to that version, aka “false positives.” As such, the information discovered by passive vulnerability systems must be managed. It must be possible to discard a vulnerability so it doesn’t continue to show up in reports.
- The vulnerabilities that are discovered may have already been remediated, but as those remediations don’t always reflect in the software version reference (the look-up key for searching vulnerability databases), some vulnerabilities continue to appear as “false positives.”
Pros and cons of active scanning
There’s only one benefit of using an active scanner, but it’s an important one. As active scanners use tests to detect the presence of vulnerabilities, the number of “false positives” (or “false negatives”) is usually very low. In other words, for a particular system, an active vulnerability scanner will provide a more qualitative result than a passive solution.
The drawbacks of active scanning are:
- Active scanners perform a series of tests over a short period of time. As a result, a large number of requests are sent directly to the systems under test, which can flood networks with large amounts of data traffic. This can affect the speed, performance, uptime and operation of the targeted system or a network segment, or may generate unwanted log files and unnecessary alerts.
- Because active scans can be intrusive, they must be carefully planned and prepared for (e.g., exceptions must be configured so the intrusion detection and response systems are activated). As a result, active scanning is resource intensive.
- Because they are labor-intensive and potentially intrusive, active scanners cannot be used to monitor entire corporate networks 24/7, so they may not be able to detect in real time new network assets in a company’s footprint. Consequently, vulnerabilities in these systems can remain undiscovered for some time, leaving the door open for malicious actors.
Conclusion
Active and passive scanners are not substitutes for each other, rather, they complement each other. While passive scanners can be used to monitor an entire corporate network on a continuous basis without much effort, active scanners can be used to periodically test critical IT and network systems that are known hacker targets. By implementing both vulnerability scanning techniques in your cybersecurity program, you can combine their strengths and mitigate their respective weaknesses, giving you a more complete understanding of your security posture.
Dries leads the marketing and product management activities at Ceeyu. Before joining Ceeyu, he worked in similar roles at Voxbone (now Bandwidth.com) and Orange. Dries also worked in management consulting (at Greenwich, now EY Parthenon). He is a B2B marketer at heart, with a very strong affinity for technology.



