14 min reading Tue May 24 2022
Subdomain enumeration tools and techniques

(this article was updated January 21st, 2023)
This blog post will cover some of the most popular tools and techniques for enumerating subdomains. We'll first introduce what a subdomain is, why you should perform subdomain enumeration on your organization and then delve deeper into tools and techniques.
What is a subdomain?
A subdomain is a second-level domain that is part of a larger domain. For example, www.ceeyu.io would be a subdomain of ceeyu.io. In this case, "www" would be the subdomain, "ceeyu" would be the root domain, and "io" would be the top-level domain (TLD).
Subdomains can be used for a variety of purposes, such as to host a blog, an e-commerce site, or even an entirely different website from the root domain. Subdomains are often used to segregate different services or functionalities within an organization.
What is subdomain enumeration?
Subdomain enumeration is the process of identifying all subdomains for a given domain. This can be useful for a variety of purposes, such as identifying potential targets for an attack, or simply for organizational purposes.
Why perform subdomain enumeration?
There are several reasons why you might want to enumerate all subdomains for a given domain:
- To identify potential targets for an attack: By enumerating all subdomains, you may be able to find subdomains that are less well-protected than the root domain or the target organization, making them more vulnerable to attack.
- To gain insights into the organization: Subdomain enumeration can give you insights into how an organization is structured, what services they offer, and so on. This information can be valuable when performing reconnaissance for a penetration test or security assessment.
- To find misconfigured DNS entries: In some cases, organizations may have misconfigured DNS entries that reveal sensitive information, such as internal IP addresses.
From an attacker's point of view, subdomain enumeration can be used to find potential vulnerabilities. For example, if an organization has a blog hosted at blog.example.com, and the blog software is not kept up to date, an attacker may be able to exploit it and gain access to the main example.com domain. Vulnerable subdomains can also be used to launch phishing attacks or other types of social engineering attacks through subdomain takeover attacks. Starting from internet-wide scan data or an IP address pool attackers can derive a list of multiple domains that might be interesting to harvest sub domains. Or they could decide to target a specific domain or multiple subdomains to start their attacks on.
Organizations can use subdomain enumeration for a variety of purposes, such as inventorying their owned domains, or identifying which domains are being used for which purposes. This can be helpful in organizational security efforts, as it can help identify potential weak points that may need to be addressed. It is also really helpful to find old, deprecated, and potentially vulnerable applications hosted on subdomains of which no one still knows why they exist or who maintains them.
Finally, it can disclose misconfigured DNS entries that can lead to a lot of information leakage, such as internal IP addresses. Maintaining your DNS records and DNS servers can prevent a lot of risk exposures or potentially devastating attacks on your organization's environment. Regularly checking your DNS record and your DNS configuration can help!
How to perform subdomain enumeration
Enumeration starts from a list of domain names and tries to find hostnames that resolve to IP addresses. This can be done by querying public DNS servers, or by looking through public records such as the WHOIS database.
There are generally two different approaches to performing subdomain enumeration: either actively or passively.
Passive subdomain enumeration
Passive subdomain enumeration is performed by using publicly available data, such as search engine results, querying DNS records on DNS servers, and so on. This data is typically collected automatically, and no interaction is required with the target domain. Some of the passive DNS enumeration techniques we'll discuss here are:
- Certificate Transparency
- Google Dorking
- DNS Aggregators
- ASN Enumeration
- Subject Alternate Name (SAN)
Certificate Transparency
Certificate Transparency (CT) is a Google initiative that was created to improve the security of SSL/TLS certificates by making them publicly available. The goal of CT is to make it easier for organizations and users to detect fraudulent or misissued SSL/TLS certificates by providing a publicly accessible log of all issued certificates.
Under CT, any SSL/TLS certificate that is issued by a Certificate Authority (CA) that participates in CT will be logged to one or more public Certificate Transparency Logs (CTLs). These logs are available for anyone to query, and they can be used to enumerate subdomains for a given domain. By searching the CTLs for a specific domain, one can find all the SSL/TLS certificates that have been issued for that domain and its subdomains. This can be useful for identifying new or unknown subdomains that may be hosted on a domain. Additionally, CT logs can also be used to monitor for SSL/TLS certificates that have been revoked or have expired, which can help organizations maintain the security of their web assets.
Moreover, CT is not limited to SSL/TLS certificates, but also it can be used to discover and monitor other types of security-related assets, such as Public Key Infrastructure-Based Authentication (PKI-Based) and others. CT logs can be used to detect unexpected certificate issuance, such as phishing or malware campaigns, and help to prevent them.
To find subdomains using CT, you can use one of the many publicly available CT log explorers, such as crt.sh or SSLMATE's CT Log Explorer. Simply enter the domain name you want to enumerate into the search box, and the tool will return a list of all subdomains that have been logged to the CT logs.
Some CT Logs search engines:
Google Dorking
Google Dorking is a powerful technique that can be used to uncover information that is not intended to be publicly available. It is a technique that leverages the power of Google search engine to find sensitive information such as website vulnerabilities, login pages, unindexed directories, and more. Google Dorking is a form of search engine reconnaissance and a very effective way to gather information about a target.
One of the benefits of Google Dorking is that it can be used for subdomain enumeration. This is done by searching for the "site:" operator in Google, followed by the target domain. For example, searching for "site:example.com" will return a list of all websites that are hosted on the example.com domain. By scanning through the results, one can find any interesting subdomains that may be hosted on the domain. This can be a useful technique for identifying potential targets for further reconnaissance or penetration testing. Additionally, Google Dorking can also be used in combination with other techniques, such as using advanced operators and searching for specific file types to uncover more specific information.
You can find more operators on the following page: Google Advanced Search Operators
Dorking is not limited to Google's search engine only, there are many other search engines available that support some form of Dorking:
DNS Aggregators
DNS aggregators are services that allow you to check multiple DNS servers at once to see if they're configured correctly. By doing this, you can find a large number of subdomains in a short time. For example, one popular free DNS aggregator is snipr.com/subdomain_finder/. Simply enter a domain into the search box and click on the "Find Subdomains" button to get a list of all subdomains for that domain. You may need to try different DNS aggregators as some will return more results than others.
Some useful online DNS tools:
ASN Enumeration
Autonomous System Number (ASN) enumeration is a process that allows you to identify all the organizations that are using a specific IP address. This can be accomplished by querying an organization's Autonomous System (AS) number from a publicly available database, such as the RIPE Database or ARIN Registry. These databases contain information about IP address allocation and mapping to organizations.
Once you have identified all of the organizations using an ASN, it is possible to further investigate these organizations by querying their nameservers. This can reveal any subdomains they may be hosting. For example, many large organizations use their domain name as their primary DNS server (e.g., www.example.com). By performing ASN enumeration on the domains in question, it may be possible to uncover interesting subdomains hosted on those domains, such as dev.example.com or intranet.example.com. This can be useful for identifying potential targets for further reconnaissance or penetration testing. Additionally, it can also be used to identify potential security vulnerabilities in an organization's infrastructure.
Subject Alternate Name (SAN)
A Subject Alternate Name (SAN) is an extension to an SSL/TLS certificate that allows multiple domain names to be associated with a single certificate. This can be used to enumerate subdomains, as each SAN typically represents a different subdomain. For example, if you have a certificate for www.example.com, the SAN might include dev.example.com, test.example.com, and so on.
To find the SAN for a given certificate, you can use a tool such as SSLMate's Certificate Inspector or Google Chrome's developer tools. Simply enter the domain name into the tool and it will return a list of all SANs associated with the certificate.
BGP (Border Gateway Protocol) Toolkit:
Or through the Regional Internet Registry (RIR) services:
- Africa: AFRINIC - Regional Internet Registry for Africa
- Asia: APNIC - Regional Internet Registry for Asia Pacific
- Europe: RIPE
- Latin America: LACNIC - Internet Addresses Registry for Latin America and the Caribbean
- North America: ARIN - American Registry for Internet Numbers
Active subdomain enumeration
Active subdomain enumeration is a method of identifying subdomains of a target domain by interacting with it directly. This is achieved by sending various types of requests, such as web requests and DNS queries, to the target domain. The data collected through these interactions is typically analyzed manually and can reveal hidden or otherwise unknown subdomains. Unlike passive subdomain enumeration, active subdomain enumeration requires direct interaction with the target domain and can be more time-consuming to perform. However, it can also yield more accurate and up-to-date results.
- Brute Force Enumeration
- Zone Transfer
- DNS Records
- Content Security Policy (CSP) Header
Brute Force Enumeration
Brute force enumeration is a method of enumerating subdomains by trying to connect to each one in turn. This can be done manually, or with automated tools such as Sublist3r and knock.
To perform manual brute force enumeration, you can try to connect to each subdomain, in turn, using a web browser or other tool. For example, if you know the main website for a domain is www.example.com, you can try connecting to subdomains such as test.example.com, dev.example.com, staging.example.com, and so on. If any of these subdomains are accessible, you will be able to enumerate them.
A more automated method of subdomain enumeration is to use a tool such as Sublist3r to perform a dictionary-based brute force attack. This can be performed by specifying a list of known subdomains, or a wordlist containing possible subdomain names, and the tool will try each one in turn.
Another automated approach to brute force enumeration is with tools like SubBrute, which uses an intelligent DNS brute forcing algorithm to reduce the search space for each query.
Here are a couple of interesting brute force wordlists:
- Jhaddix’s all.txt
- Daniel Miessler’s DNS Discovery
- Commonspeak2
- rajesh6927/subdomain-bruteforce-wordlist
Zone Transfer
A zone transfer is information about all existing name servers and domains for a given domain. This can be used to identify all existing subdomains for that domain.
DNS zone transfer is commonly blocked on modern networks using firewall rules to filter DNS requests, so this method may not be effective in all cases. Additionally, some DNS servers will only perform a DNS zone transfer to authorized hosts, so it may be necessary to spoof the source IP address of the request in order to perform a successful transfer.
Content Security Policy (CSP) Header
The Content Security Policy (CSP) header is a security measure that can be used to restrict the sources from which a browser can load content. This includes JavaScript, CSS, HTML, and other types of files.
If a CSP header is present on a website, it may be possible to enumerate subdomains by trying to load resources from those subdomains. For example, if you try to load a stylesheet from test.example.com and the CSP header is present, it will block the request and return an error. This can be used to identify subdomains that are accessible.
CSP headers can be found in the HTTP response headers of a website. To view the headers for a given website, you can use a tool such as Google Chrome's Developer Tools or Firefox's Web Developer Tools.
These are just some of the most common methods for subdomain enumeration. There are many others, and new techniques are always emerging as attackers become more sophisticated. Ultimately, the best way to conduct subdomain enumeration is often to combine multiple techniques and tools in order to get the most comprehensive results.
Wildcard domains present
Wildcard domains present additional challenges and opportunities for subdomain enumeration. Because they allow any subdomain to be accessed, they make it more difficult to identify valid subdomains that are actually in use. However, because every subdomain can be accessed, this also provides a window of opportunity for attackers to find previously unknown vulnerabilities or access sensitive data. As such, it is important for organizations to carefully manage their wildcard domains and ensure that no unused subdomains remain exposed. A telltale resides in a wildcard SSL certificate. A wildcard certificate is a digital certificate that is applied to a domain and all its subdomains. Wildcard notation consists of an asterisk and a period before the domain name. Secure Sockets Layer (SSL) certificates often use wildcards to extend SSL encryption to subdomains. When such a wildcard is noted on the certificate level chances are that you'll find a bunch of subdomains below it.
Some additional sub domain enumeration tools to consider
Amass
One of the best known sub domain enumeration tools freely available is OWASP Amass. This tool is specifically designed to identify sub domains and sub domain relationships. It uses a variety of techniques, such as search engine harvesting, DNS enumeration, brute force attacks, and more.
SubBrute
Another powerful sub domain enumeration tool available is SubBrute. This tool performs dictionary-based brute force attacks in order to find the most effective combinations of words for each query. Additionally, it has built-in features that allow you to customize the way that queries are performed based on your specific needs or requirements. Although it is rather old it still yields good results.
DNSrecon
DNSrecon is another popular free sub domain enumeration tool that can be used for manual or automated discovery of subdomains. This tool has numerous advanced features and options that allow you to customize your queries and search for subdomains in a variety of different ways. DNSRecon is embedded in the excellent Kali Linux Penetration Testing distribution.
Sublist3r
Sublist3r is another popular tool that can be used for both manual and automated subdomain enumeration. This tool uses a variety of search engines, such as Google, Bing, Yahoo, and more, in order to find subdomains for a given domain. Additionally, it has the ability to perform brute force attacks with a user-specified list of words or with a wordlist from Daniel Miessler's seclists project.
Massdns
Massdns is a high performance DNS resolver designed specifically for mass DNS enumeration. This tool can be used to resolve large numbers of domains or subdomains very quickly. It can also be used to perform brute force attacks with a user-specified list of words or with a wordlist from the seclists project.
SubFinder
SubFinder is a relatively new tool that has quickly become very popular for subdomain enumeration. This tool uses passive sources, such as search engines, crt.sh, Netcraft, and more, in order to find subdomains. This one as well can use wordlists for brute-force attacks.
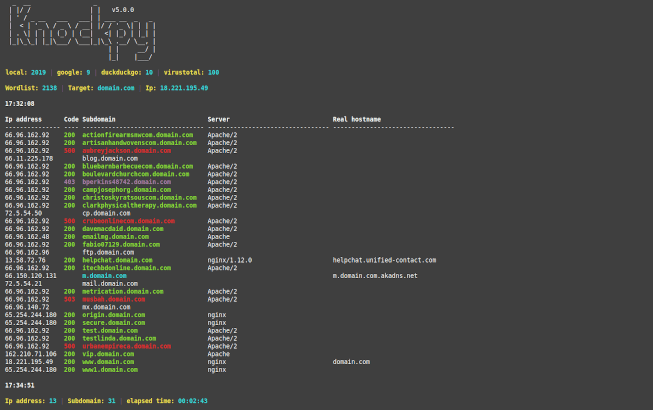
Knock
Knock is another tool that can be used for both manual and automated subdomain enumeration. This tool uses a variety of techniques, such as brute force attacks, permutations, and more. Additionally, it has the ability to integrate with the excellent Amass tool for even more comprehensive results.
SubDomainizer
SubDomainizer is a simple yet effective subdomain enumeration tool. This tool uses Google's search engine to find subdomains.
GoBuster
GoBuster is a command-line tool for performing directory and file enumeration on web applications. It can be used to discover hidden files, directories, and other resources that may not be readily apparent from the website's public-facing pages. Gobuster uses a wordlist to brute-force the URLs and directories of a website and can also be used to perform subdomain enumeration. Next to this it is also excellent at enumerating subdomains (use the DNS parameter) with wildcard support.
Gobuster's main advantage is its speed and versatility, it can be run on multiple threads, it can be used with a large wordlist and it can be used in conjunction with other tools like Nmap, Burp Suite, and others.
Wrapping up
To conclude there are many other tools available for subdomain enumeration beyond those listed here. The best way to find the right tool for your needs is to experiment with a few different ones and see which one works best for you. There is no single "best" tool for this task, as each one has its own advantages and disadvantages. Ultimately, the best way to conduct subdomain enumeration is often to combine multiple techniques and tools in order to get the most comprehensive results.
Regardless of the specific tools or techniques that you use, it is important to always conduct subdomain enumeration in a careful, methodical manner. Failing to do so can result in missed opportunities, false positives, and other problems that can compromise your overall security posture. By taking the time to utilize these methods and tools effectively, you can help ensure better protection for your organization moving forward.
How Ceeyu can help
We have built several passive and active subdomain enumeration techniques right into Ceeyu's scanning engine. This makes it easy for our customers to find the subdomains on one or more of their domains. Moreover, when we find a web application behind the domain name we'll take a screenshot so you can easily and visually identify what is hosted on it:
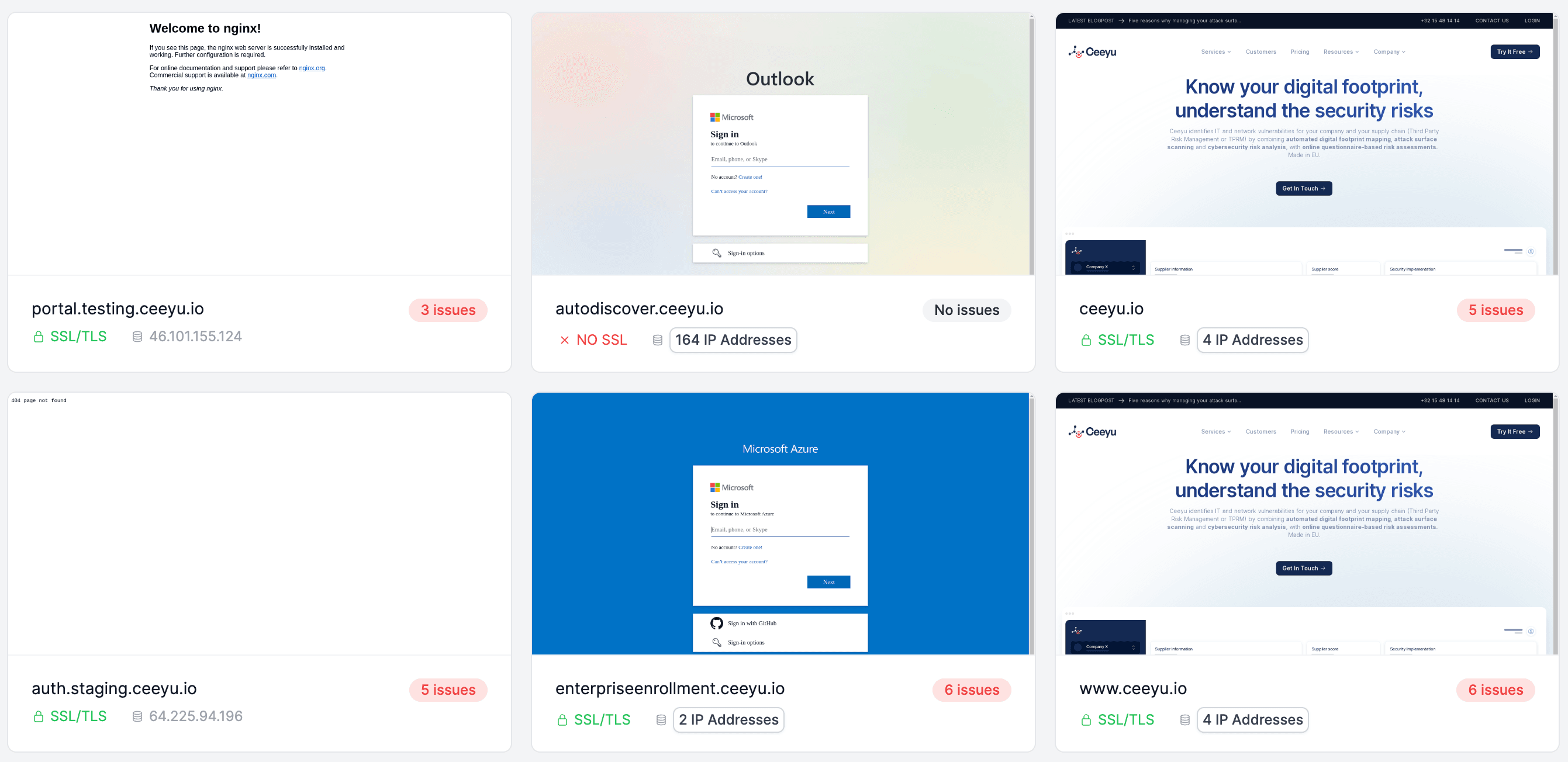
These subdomains are then part of additional security testing and digital footprint enumeration to give all the insights required to understand and manage your attack surface.
Give us a shout if you'd like to know more and start a free trial!
Jimmy is the founder, CEO and CTO of Ceeyu. Prior to founding Ceeyu, Jimmy was responsible for cybersecurity programs at large financial institutions and consulting company EY. Jimmy started his career as a security engineer. His duties included installing and managing firewalls, scanning infrastructure for vulnerabilities, and performing pen testing and ethical hacking.



