
A record 26,447 software security flaws were reported in 2023, up 1500 versus 2022
Infosecurity Magazine
Vulnerability management
Vulnerability management is the process of identifying, evaluating, prioritising and remediating security vulnerabilities in IT and network systems and the software running on them. This activity is a key component of attack surface management and is vital for companies to eliminate potential threats and minimize their "attack surface." The digital footprint of companies is anything but static. It’s constantly changing to encompass new technologies, systems, and services. This makes vulnerability management a continuous activity, not just a yearly project.
New digital vulnerabilities are being discovered on a nearly daily basis, accounting for thousands of new threat vectors every year that may be exploited causing significant problems for organizations across essentially every industry. In addition, systems and services are growing more complex and keeping all interconnected software continuously up to date with the latest patches and updates is simply impossible. Vulnerability management helps in identifying the most pressing security risks.

Infosecurity Magazine
Ceeyu offers two types of vulnerability scanners.
Our passive, non-intrusive vulnerability scanner starts from the software type and version information we find when scanning your network from the outside, aka software fingerprinting. In CPE (Software), CWE (Weakness) and CVE (Vulnerability) databases, we look up the potential vulnerabilities we find for the software you’re using.
Our active vulnerability scanner sends transmissions of “test traffic” to selected nodes or endpoints on your enterprise network. Our platform examines the responses received from these nodes to assess if vulnerabilities are present in the selected nodes. Since the active vulnerability scanner integrates with our digital footprint discovery service, customers can target an active scan to a selection of IP addresses or subdomains in their footprint. The service can perform more than 100,000 vulnerability tests, depending on the type of services discovered on the target. An active scan can be run ad hoc, or can be scheduled at a time of your choice.
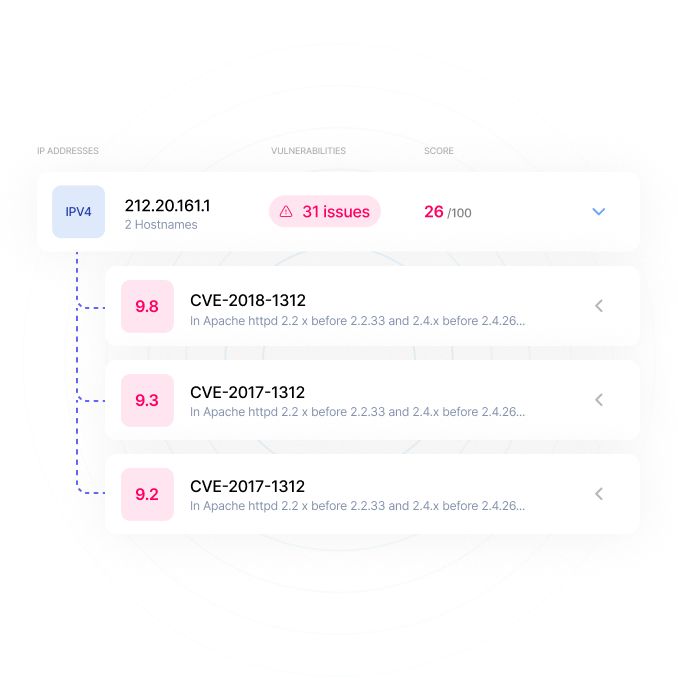
Don't bother looking up and entering IP addresses yourself to scan for vulnerabilities. Our Digital Footprint mapping service uncovers all externally visible network assets, our Attack Surface management service identifies all vulnerabilities among these assets. Setting up a scan is as simple as selecting IP addresses and/or subdomains that are part of our digital footprint or attack surface.
Our passive, non-intrusive vulnerability scanning service periodically scans your network to find new software in use and new potential vulnerabilities.
Ceeyu 's active vulnerability scanner simulates attacks on your network to expose network security vulnerabilities that a hacker could exploit. Since this is unlikely to go unnoticed by your intrusion detection systems, this type of scan must be carefully planned and prepared. To support this, Ceeyu allows you to perform the scan "ad hoc," or schedule the scan at your convenience.
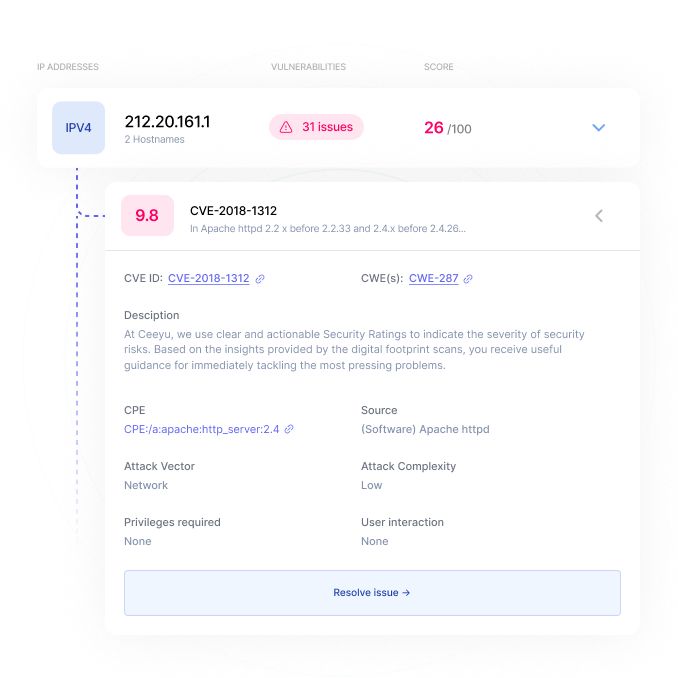
The Ceeyu platform offers all the tools you need to identify and monitor the presence of vulnerabilities in your digital footprint