6 min reading Mon Sep 04 2023
How to search for keywords in hostnames, domain names and URLs
Regularly checking whether your company name (or registered product brand names) appear in domain names is a healthy exercise to detect two types of problems that can compromise your cybersecurity defenses:
- Domain name spoofing: Website spoofing occurs when an attacker builds a website with a URL that closely resembles, or even copies, the URL of a legitimate website that a victim knows and trusts. In addition to copying the URL, the attacker can also copy the content and style of a Web site, complete with images and text.
- Shadow IT, mostly Shadow SaaS: SaaS applications that are in use without the knowledge of IT or security. Shadow SaaS is often called "business-led SaaS" and happens when users create SaaS accounts outside the official IT purchasing process. These applications often use URLs that contain the company name or product brand names.
To search the DNS for keywords in domain names or host names, you can use different methods and tools depending on your operating system or preferences and depending on your purpose.
Search for keywords in domain names with an exact match (aka, check if a domain is in use)
In this scenario, we are looking for the use of the word "Ceeyu" in a domain name, e.g., Ceeyu.io
Command line tools
To search for a specific domain name, you can use the nslookup command on Windows computers. The command returns the A record for the domain you queried for, so if the command returns one or more IP addresses, this indicates that the domain name is in use.
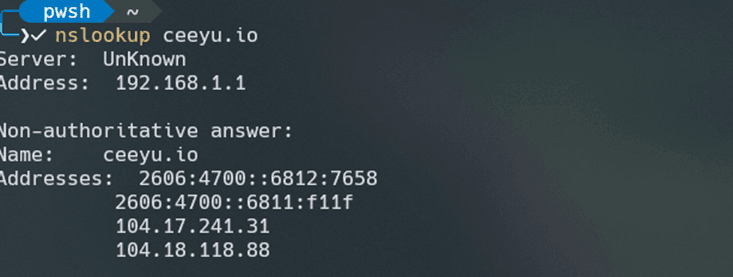
To look up a specific record type for a domain, you can add the command -type followed by the record type (A, CNAME, MX, SRV, PTR, NS, ANY). To get to the same result as the example here above, the command to be used would be nslookup -type=A ceeyu.io.
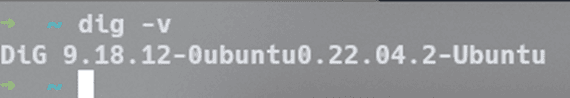
The equivalent command for Mac/Linux is dig. Before using this command, make sure dig is installed on your OS. This can be done with the dig -v command in the terminal. If it is installed, the output will look like this:
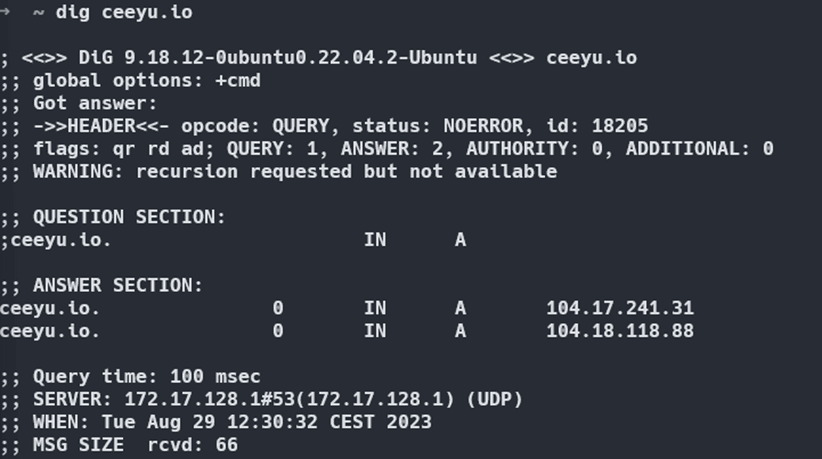
Once dig is installed, the dig Ceeyu.io command gives you the IP address of the A record for the domain you are looking for.
OK, this looks super basic, but it gets more interesting if you add some Powershell (Windows) or bash or zsh (Mac/Unix) scripts. By creating a wordlist with all possible domain extensions and scripting the nslookup or dig command with the contents of the wordlist (dig ceeyu.<insert from wordlist>). Using grep on the output of the script, extract the domain names that contain IP addresses, or the domain names for which no "nonexistent domain" was returned. These are the domains that are in use.
Online tools
If you have no experience with command lines and scripts, you may choose to search online with tools such as whatsmydns or dnschecker.
Alternatively, you may consider domain name brokers, such as namecheap or instantsearchdomain. The disadvantage of using such commercial tools is that the search information collected can be used for commercial purposes.
Most hosting providers are also domain brokers and offer DNS lookups in their service management interface.
The disadvantage of the online tools is that none of them offer the ability to search all domain extensions. Unlike the scripting options described above, online lookups cannot be automated and are limited to the search options the broker offers.
Search for keywords in host names and domain names
This is where it gets more interesting. In this example, we are looking for the use of "Ceeyu" in a hostname (e.g., Ceeyu.zendesk.com) or a domain name (eg. www.ceeyu-security.com). This can be done in three ways.
“The old way”, which no longer works in most cases: start from a Zone Transfer.
A zone transfer is the process of copying DNS data from a primary DNS server. Since zone transfers can expose sensitive DNS information, including host names, IP addresses and possibly other records, to unauthorized parties, who could use them to fine-tune an attack on your network. Zone transfers are therefore controlled and restricted to authorized servers by whitelisting their IP addresses and by increasingly other security measures such as DNSSEC (DNS Security Extensions) and TSIG (Transaction Signature).
A zone transfer can be performed/attempted with the dig and nslookup command described above, in combination with the AXFR DNS query type. For more information and for how to’s, please refer to this article for Mac/Linux and this article for Windows.
Using a Passive DNS database
Passive DNS is a method used to collect and store historical DNS data, including information about the mapping between domain names and IP addresses. Unlike traditional or active DNS, in which DNS servers respond to real-time queries, passive DNS focuses on capturing and recording DNS resolutions that occurred in the past. Passive DNS systems work by observing and capturing DNS traffic on the network or by collecting DNS data from various sources such as DNS server logs, packet captures or other monitoring mechanisms. This data is then stored in a database, providing a historical record of DNS resolutions over time.
Some places to find these passive DNS databases:
• Circl
• Securitytrails
• Censys
The disadvantage of using passive DNS databases is that they are incomplete and do not contain the most recent information. It can take days, weeks, or months for a hostname to appear in (or disappear in the case of a hostname being taken out of service) a passive database.
Using google dorking
Google Dorking, also known as Google Hacking, is a technique used by information security professionals and hackers to find specific information on the Internet using advanced searches on Google's search engine. This technique involves the use of specific search terms, operators and filters to uncover sensitive or hidden information that may not be easily accessible through traditional search methods.
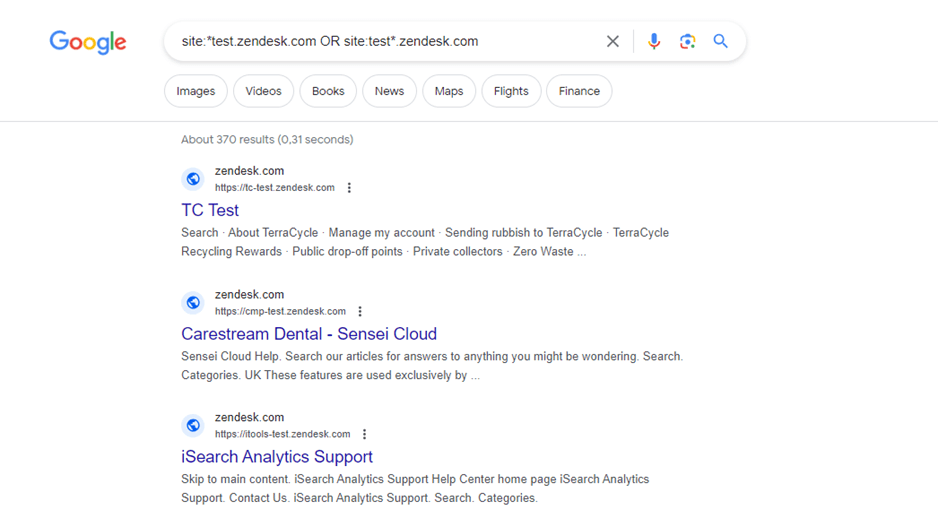
For example, the search site:*test.zendesk.com OR site:test*.zendesk.com will give you a list of all subdomains of zendesk.com containing the word “test”.
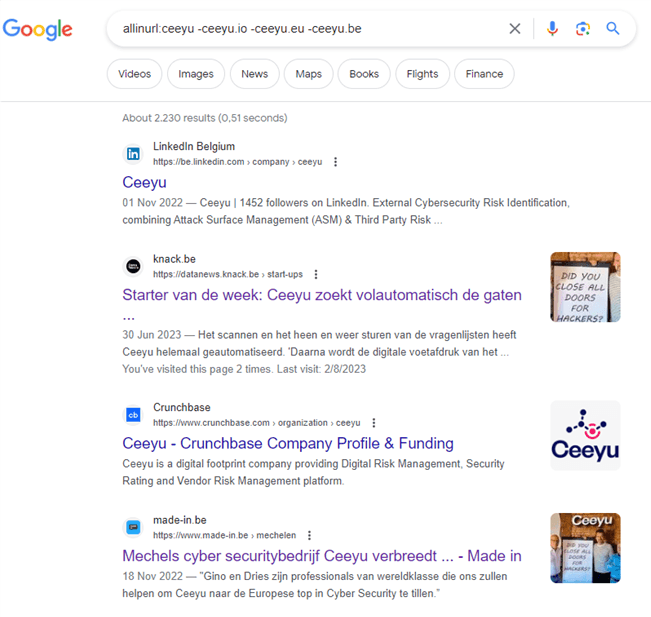
The search allinurl:ceeyu -ceeyu.io -ceeyu.eu -ceeyu.be will result in a list of all URLs containing the word "Ceeyu" except ceeyu.io, Ceeyu.be and Ceeyu.eu. The search results include both subdomains and URLs with the keyword in the path (e.g., linkedin.com/company/Ceeyu).
For a fairly complete list of Google search operators, please refer to this page.
If you want to extend the search with scripts, or automate the search to integrate it with an application, or to run it periodically, you can use a SERP (Search Engine Results Page) API. These applications scrape search results and make them available through an API. Some providers of these APIs:
• SerpAPI
• Brightdata
• Serphouse
Search for variations of a keyword in domain names (aka typoquatting)
Typosquatting, also known as brandjacking or URL hijacking, is a form of cyberattack in which malicious people register domain names that resemble legitimate domain names. These malicious domain names are designed to take advantage of typographical errors, such as transpositions, misspellings or other common mistakes users make when entering a Web site address into their Web browser.
So how do you know if such domain names exist and are being misused by malicious people? For this you can use a domain name permutation engine, such as:
• DNStwist
• URLcrazy
• Ceeyu.io
As part of its attack surface management service, Ceeyu continuously scans for domain name permutations, checks for them and adds a screenshot to the result, allowing customers to judge whether the Web site is malicious or not.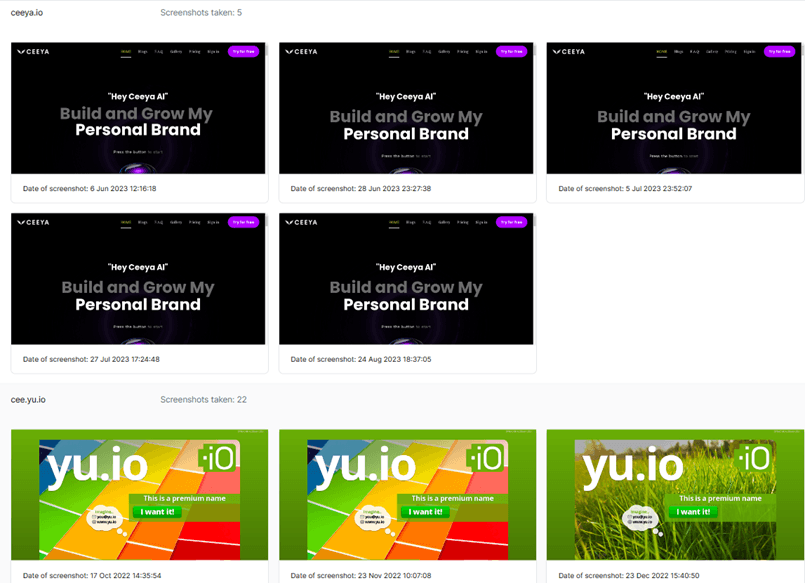
Do you want to know more about domain name enumeration? Read our blogpost on this topic. Interested to explore Ceeyu’s EASM (External Attack Surface Management) platform? Register a free account or get in touch!
Image by GraphiqaStock on Freepik
Dries leads the marketing and product management activities at Ceeyu. Before joining Ceeyu, he worked in similar roles at Voxbone (now Bandwidth.com) and Orange. Dries also worked in management consulting (at Greenwich, now EY Parthenon). He is a B2B marketer at heart, with a very strong affinity for technology.



