6 min reading Tue Nov 07 2023
Will your company be subject to NIS2?

EU countries have until Oct. 17, 2024, to transpose their measures into national legislation, after which NIS2 will formally replace NIS1. From then on, between 100,000 and 150,000 companies in the EU will be legally required to have implemented cyber security controls, for their own IT and network systems, as well as for their suppliers, and to report incidents. Will your company be among them?
A little history
The NIS regulation is the Network and Information Systems Regulations. The first regulation, now referred to as NIS1 was adopted by the EU Parliament in July 2016 and came into force on May 10, 2018. At the time, it was the world's first cybersecurity legislation. The goal of the first NIS Directive (EU 2016/1148) was to achieve a high common level of cybersecurity across the European Union.
Although the directive increased member states' cybersecurity capabilities, its implementation proved difficult, resulting in fragmentation at different levels within the internal market. One of the major problems with the NIS1 Directive was its ambiguous wording and the excessive autonomy given to member states to determine which entities fell within its scope. National authorities could define entities based on different criteria (market size, number of users, geographic coverage of the service, etc.), but they were not allowed to do so. This obviously led to inconsistencies in the implementation of the Directive in all member states.
On Jan. 16, 2023, the second NIS Directive (EU 2022/2555) (known as NIS2) came into force to replace the NIS1 Directive. NIS2 improves and extends NIS1 in several ways, including by defining which companies the directive applies to. Read more about the key changes in this blogpost. NIS 2 addresses the problem of too much autonomy by introducing a list of sectors and company size criteria (turnover, number of employees) that should be considered essential or important entities and fall within the scope of NIS 2. However, member states still have some degree of automation, more specifically when deciding whether small businesses in specific sectors are also subject to NIS2. More on this topic below.
More history: DORA
It should be noted that NIS is not the only cybersecurity regulation, there is also DORA (Digital Operational Resilience Act, EU 2020/0266), the EU cybersecurity regulation for the financial sector, that entered into force on 16 January 2023 and will apply as of 17 January 2025.
DORA applies very broadly and covers all authorized European financial entities, 20 types in total (including banks, investment firms, insurers, accounting firms and trading platforms), and their critical ICT suppliers. There are several differences between DORA and NIS2, but in general, DORA is more comprehensive and stringent than NIS2, so companies that comply with DORA also comply with NIS. For organizations that are subject to DORA - and only if they are - DORA prevails over NIS2.
The industries to which NIS 2 applies
The NIS 2 thus eliminates the classification and distinction between operators of essential services - so-called "OEDs" - and providers of digital services - so-called "DSPs." Instead, the NIS 2 makes a distinction between "essential entities" and "important entities".
Essential service operators were already defined in NIS 1, but some sectors have been added in NIS 2. This is the list of sectors to which NIS 2 will apply:
- Energy (electricity, oil and gas, covering production, storage and transmission activities - hydrogen as added by NIS 2)
- Drinking water
- Wastewater (collection, disposal or treatment of municipal wastewater, domestic wastewater or industrial wastewater)
- Transportation (air, rail, water, road)
- Banks and financial markets (also regulated by DORA)
- Digital infrastructure providers (Internet nodes; DNS service providers; TLD name registries; cloud computing service providers; data center service providers; content delivery networks; trust service providers; providers of public electronic communication networks and public electronic communication services)
- ICT service management (managed service providers and managed security service providers)
- Governments (central and regional, the latter being risk-based only but excluding defense or national security and law enforcement, as well as the judiciary, parliaments and central banks)
- Healthcare (hospitals but under NIS2 now also includes reference laboratories, manufacturers of medical devices or pharmaceutical preparations and others)
- Aerospace
New in NIS 2 is the introduction of "important" entities, targetting the following sectors:
- Postal and courier services
- Waste management
- Digital service providers (online marketplaces, online search engines and social networking platforms)
- Research organisations (excluding education)
- Production and distribution of chemicals
- Wholesale and industrial food production and processing
- Manufacturing of:
- Medical devices
- Electrical equipment
- Motor vehicles, trailers, and semi-trailers
- Machinery and equipment
This list is not exhaustive, as member states may add entities in other types of industries to the list of important or even essential entities. For example, large-sized (but potentially also medium-sized) accounting firms may be categorized as important entities, particularly if they provide services to essential sectors (like banking or finance) or if their services are deemed crucial for the economy..
The company size criteria in NIS 2
Under NIS 1, member states were responsible for determining which entities met the criteria to qualify as operators of essential services. NIS 2 addresses this shortcoming by introducing a size cap rule as the rule for determining regulated entities. A distinction is made between:
- Large entities: more than 250 employees or a turnover of more than 50 million euros
- Medium-sized entities: more than 50 employees or a turnover of more than 10 million euros
- Micro or small entities: < 50 employees and a turnover of less than €10 million
Exceptions are however possible at the member state level:
- Medium-sized entities in essential sectors are "important" unless considered "essential" by the Member State (some exceptions apply: telecommunications, DNS, TLD providers are always essential)
- Micro and small entities may be considered important or even essential by member states, but this must be exceptional.
Here is a more visual overview of sectors, entities by size and possible exceptions: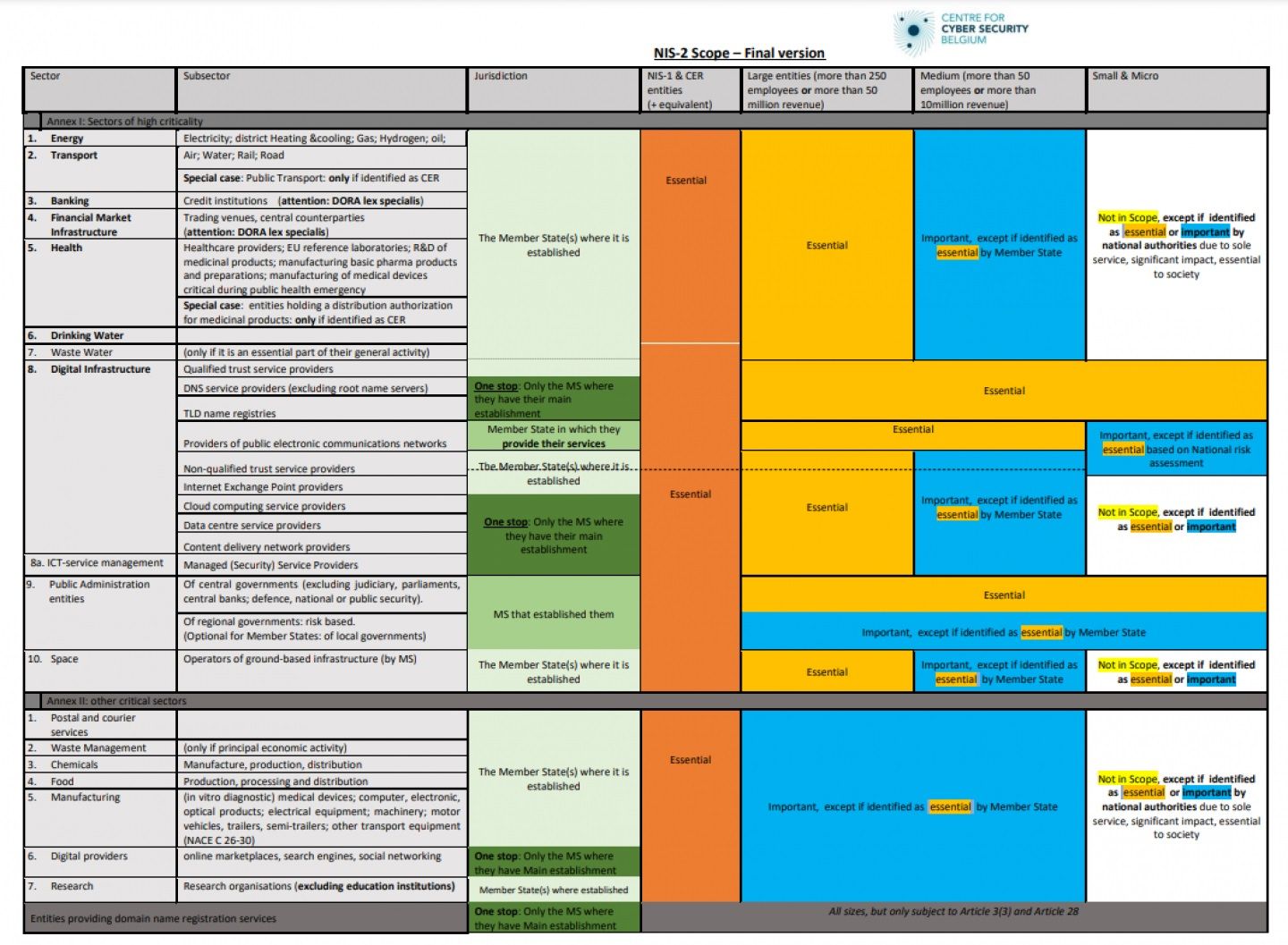
Source: Center for Cybersecurity Belgium.
Geographical applicability
Under the NIS2 Directive, essential and important entities are under the jurisdiction of the member state in which they provide their services.
If the entity provides services in more than one member state, it must be under the jurisdiction of each. For entities whose service is provided or depends on activities outside the EU, they must ensure the continuity of their EU services in the event of disruption to their activities outside the EU.
Conclusion
NIS 2 addresses the problem of too much autonomy by introducing a list of sectors and company size criteria (turnover, number of employees) that should be considered essential or important entities and fall within the scope of NIS 2.
However, there are still concerns about the autonomy problem in NIS2 regarding:
- Small enterprises (SMEs): Member States may "identify smaller entities with a high-security risk profile". This type of autonomy may lead to inconsistency and problems for SMEs operating in different member states, as they may be covered in one member state and not in another.
- Medium-sized companies: may be considered 'essential' rather than 'important' in some target segments by national authorities. As a result, a medium-sized company may be considered ‘important’ in one country and ‘essential’ in another.
To what extent this will be problematic will become apparent in the coming months as member states announce their interpretation of the NIS2 directive in the form of national legislation. We can only keep our fingers crossed and hope that there has been sufficient consultation among member states so that the number of discrepancies remains limited and workable for multinational companies.
About Ceeyu and NIS 2
Ceey's SaaS platform and professional services are key components of compliance with the NIS 2 requirements with regard to managing and reporting vulnerabilities (through passive scanning - aka external attack surface management and or active scanning techniques, and penetration tests) and supply chain security risk management.
Dries leads the marketing and product management activities at Ceeyu. Before joining Ceeyu, he worked in similar roles at Voxbone (now Bandwidth.com) and Orange. Dries also worked in management consulting (at Greenwich, now EY Parthenon). He is a B2B marketer at heart, with a very strong affinity for technology.



